Why Decrypt HTTPS Traffic with Wireshark?
This tutorial is intended for security professionals performing traffic analysis to decrypt HTTPS traffic with Wireshark. It assumes you are familiar with basic Wireshark usage and use Wireshark version 3.x. We often encounter encrypted traffic when reviewing suspicious network activity because most websites use the HTTPS protocol. Just like websites, various types of malware also use HTTPS. Understanding the content of traffic after an infection is crucial when analyzing PCAPs related to malware activity.
This Wireshark tutorial explains how to use HTTPS log files to decrypt HTTPS traffic from PCAPs in Wireshark. The log contains HTTPS encryption key data. With this key log file, we can decrypt HTTPS activity from the PCAP and view its contents. The tutorial uses the examination of HTTPS activity from a Dridex malware infection as an example.
Note: Download the PCAP and key log files used in this tutorial here.
https://github.com/pan-unit42/wireshark-tutorial-decrypting-HTTPS-traffic
Warning: The PCAP used in this tutorial contains Windows-based malware. There is a risk of infection if using a Windows machine. We recommend viewing this PCAP in a non-Windows environment (e.g., BSD, Linux, or macOS) whenever possible.
What is Encrypted Traffic?
In the mid-to-late 1990s, the most common protocol used by websites was the Hypertext Transfer Protocol (HTTP), which generated unencrypted web traffic. However, as security concerns grew, websites began switching to HTTPS, and nowadays, HTTP traffic from web browsing is rarely seen.
HTTPS essentially is an encrypted communication tunnel containing HTTP traffic. These tunnels initially used Secure Sockets Layer (SSL) as the encryption protocol. Today, most HTTPS traffic uses Transport Layer Security (TLS).
How to Decrypt HTTPS Traffic with Wireshark
1. HTTPS Web Traffic
HTTPS traffic usually displays a domain name. For example, when viewing https://www.wireshark.org in a web browser, the PCAP will show www.wireshark.org as the server name for this traffic in the customized Wireshark column display. Unfortunately, we do not know other details such as the actual URL or data returned from the server. TCP streams will not show the content of this traffic as it is encrypted.
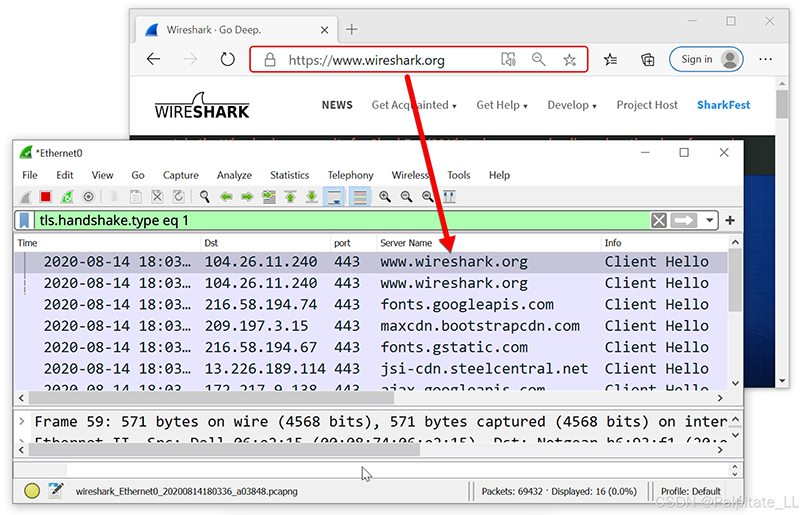
2. Encrypted Key Log Files
An encrypted key log is a text file, as shown in the image.
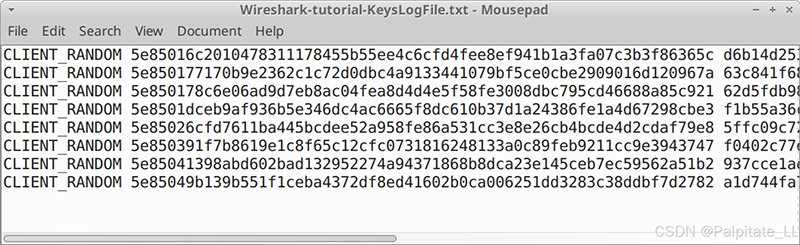
These logs are created using Man-in-the-Middle (MITM) techniques at the time of initial PCAP recording. If such a file was not created during the recording of the PCAP, decrypting the HTTPS traffic in the PCAP will not be possible.
3. PCAP Example with Key Log File
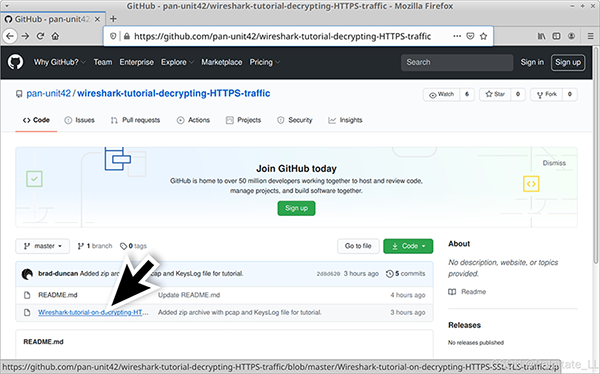
This GitHub repository provides a password-protected ZIP archive containing the PCAP and its key log file. Go to the GitHub page, click on the ZIP archive entry, and download it as shown in the image. Notably, the PCAP included in this ZIP archive provides access to a Windows-based malware sample when decrypted with the key log. As always, we recommend proceeding with caution and following the tutorial steps in a non-Windows environment.
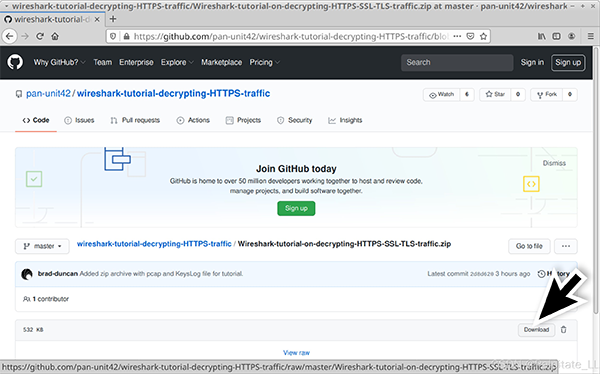
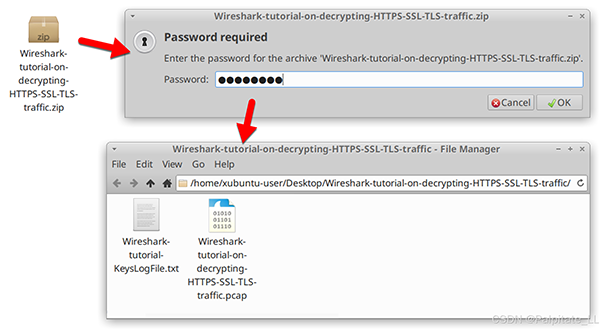
Use “infected” as the password to extract the PCAP and key log files from the ZIP archive. This will provide two files as shown in the image.
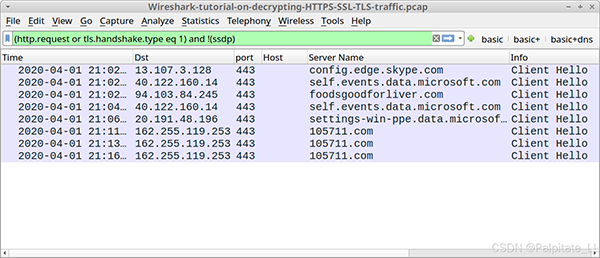
4. HTTPS Traffic Without Key Log File
Follow the instructions from the previous tutorial on Wireshark filters, using basic network filtering. For Wireshark 3.x, the basic filter is:
(http.request or tls.handshake.type eq 1) and !(ssdp)
This PCAP is from a Dridex malware infection on a Windows 10 host. All web traffic (including infection activity) is HTTPS. Without the key log file, we can only see the IP address, TCP port, and domain name as shown in the image.
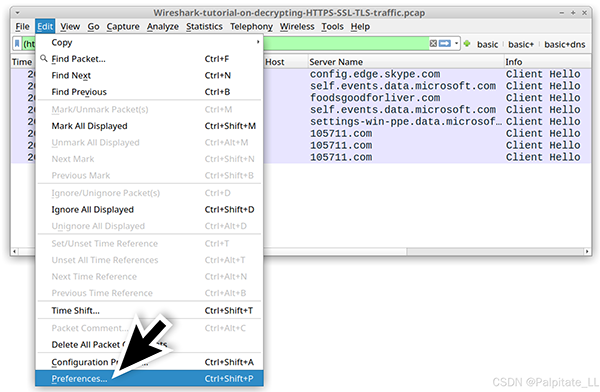
5. Loading the Key Log File
Open in Wilshack
Wilsak – Tutoriar – En – De Kripting – Heteps – S. Tetrafik – Pukapp. Then use the menu Edith – > Preference to bring up the Preference menu, as shown in the image.
On the left side of the Preferences menu, click Protocol, as shown in the image.
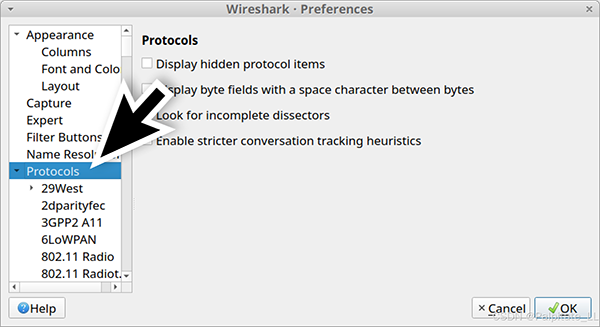
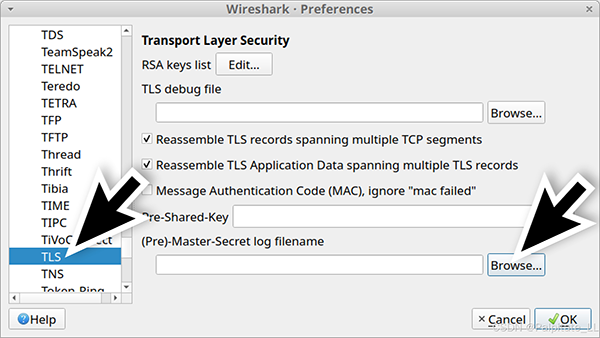
If you are using Wireshark version 2.x, scroll down until you find SSL and select it. If you are using Wireshark version 3.x, scroll down to TLS and select it. Once you select SSL or TLS, you should see a line (Pre)-Master-Secret log filename. Click on the “Browse” button and select the name named “Browse”.
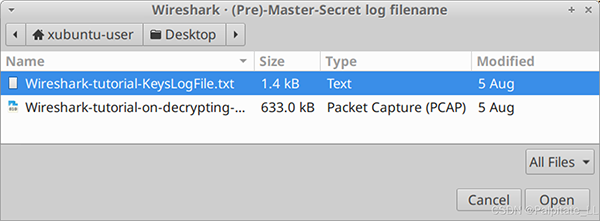
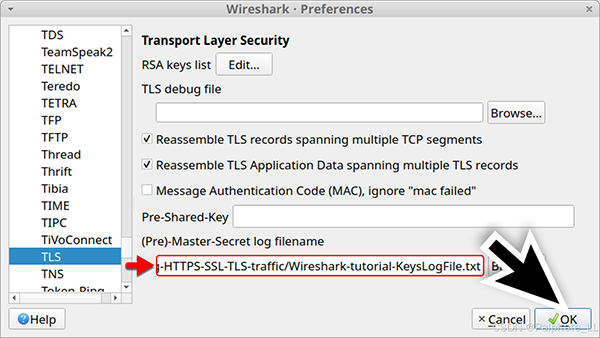
Wireshark-Tutorial-KeysLogFile.txt key log file, as shown in the image.
6. HTTPS Traffic with Key Log File
After clicking “OK,” the Wireshark column display will now list decrypted HTTP requests under each HTTPS entry when using basic filtering as shown in the image.
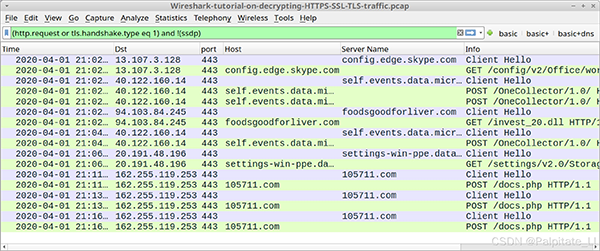
In this PCAP, we now see HTTP requests to the previously hidden domains microsoft.com and skype.com within the HTTPS traffic. We also identified the following traffic caused by the Dridex infection:
foodsgoodforliver[.]com – GET /invest_20.dll
105711[.]com – POST /docs.php
The GET request to foodsgoodforliver[.]com returned a Dridex DLL file. The POST request to 105711[.]COM is communication between the infected Dridex Windows host and Command and Control (C2).
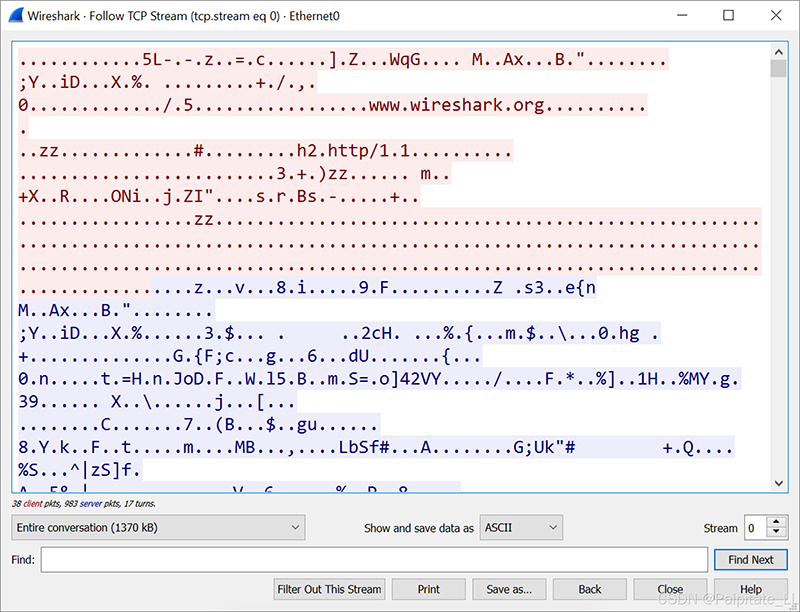
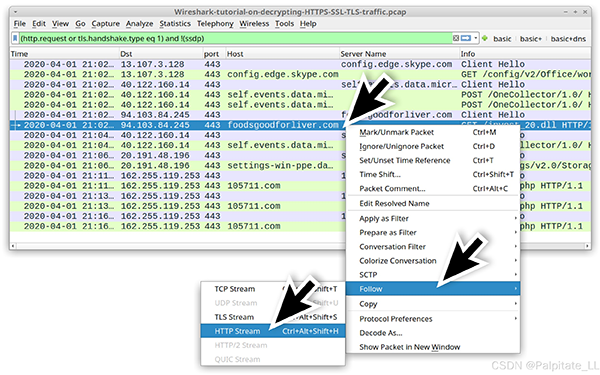
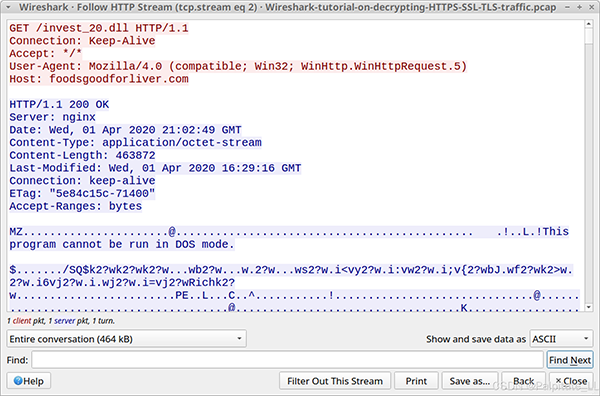
We can examine the traffic by following the HTTP stream. Right-click the line to select it, then left-click to bring up the Follow HTTP Stream menu. The image shows an example of the HTTP stream for a GET request to foodsgoodforliver[.]com.
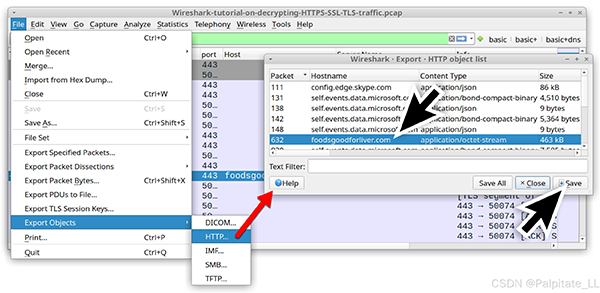
Since we have the key log file for this traffic, we can now export this malware from the PCAP. Use the menu path File –> Export Objects –> HTTP to export this file from the PCAP as shown in the image.
If you are in a BSD, Linux, or macOS environment, open a terminal window and use the file command to confirm it is a DLL file. Then use shasum -a 256 to obtain the SHA256 hash of the file as shown in the image.
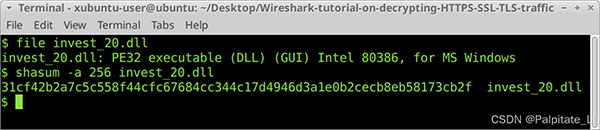
The SHA256 hash for this malware is:
31cf42b2a7c5c558f44cfc67684cc344c17d4946d3a1e0b2cecb8eb58173cb2f
Searching this hash online should yield results from at least two publicly available online sandbox environments.
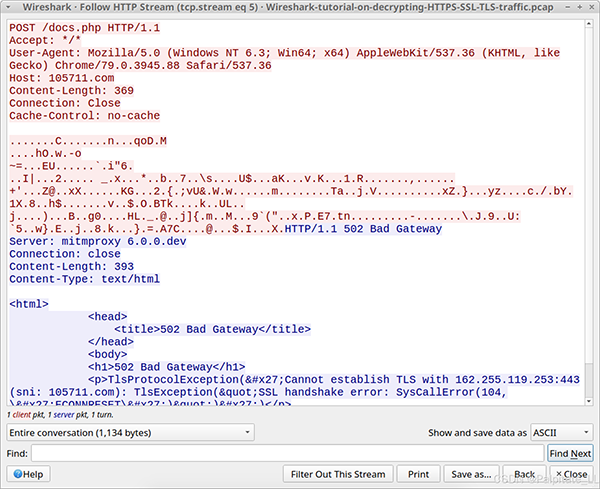
Finally, we can review the C2 traffic for this Dridex infection. Use basic network filtering and follow the HTTP stream of one of the POST requests to 105711[.]com. The image shows an example of one HTTP stream.
Conclusion
This tutorial explained how to use a key log text file to decrypt HTTPS traffic in a PCAP using Wireshark. If a key log file was not created at the time of the initial PCAP recording, it will not be possible to decrypt HTTPS traffic from that PCAP in Wireshark.



