Network engineers frequently face challenges in synchronizing VLAN information across switches in enterprise networks. This synchronization is crucial to ensure that all switches can forward data accurately. In smaller enterprise networks, administrators can simply log in to each switch to configure and maintain VLANs. However, employing VCMP can streamline this process, allowing for centralized management of VLANs and reducing the need for manual configuration.

However, in large enterprise networks, there are many switches and a large amount of VLAN information needs to be configured and maintained. If you only rely on manual operations, the workload is huge and the configuration consistency cannot be guaranteed.
How to solve this problem? That’s what I want to talk to you about today.
What is VLAN?
VLAN, or virtual local area network, abstracts the concept of a local area network by providing data link connections for subnets.
In an enterprise network, an enterprise-class switch generally has 24 or 48 ports, and the terminals connected to these interfaces physically form a broadcast domain.
If the broadcast domain is too large, a large number of broadcast messages will flood the network, reducing the available network bandwidth and the security of the broadcast domain.
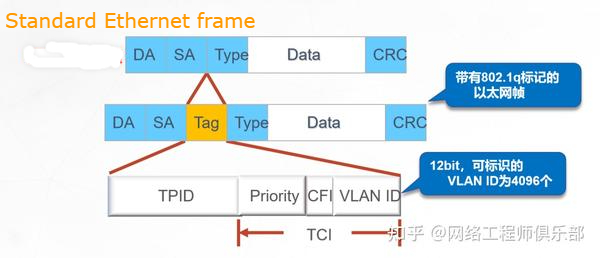
At this time, VLAN technology can be used on the switch to divide multiple logical broadcast domains.
Each broadcast domain is isolated at Layer 2, and terminals between different VLANs cannot access each other at Layer 2.
One or more network switches that can support multiple independent VLANs, thereby creating subnetted Layer 2 data links, usually composed of one or more Ethernet switches.
VLANs allow network engineers to easily segment a single switched network to meet the functional and security requirements of their systems without running new cables or making major changes to their current network infrastructure.
How to implement centralized management of VLAN?
To solve the above problems, VCMP can be used to implement centralized management of VLANs.
In this way, you only need to create or delete VLANs on one switch, and these changes will be automatically notified to all switches in the specified range so that these switches can synchronize VLAN creation, deletion, and other actions without manual operation.
This reduces the workload of modifying the same data on multiple switches and ensures the consistency of the modification.
What is VCMP?
VLAN centralized management protocol uses a domain to manage switches. This domain is called a VCMP management domain.
The attributes of a device are determined by role definition, which is called a VCMP role. VLAN centralized management protocol defines four roles: server, client, transparent, and silent.
1. VCMP management domain
A VLAN management domain consists of a group of switches with the same domain name that are interconnected through trunk or hybrid link interfaces.
Each switch in the same domain must use the same domain name, and a switch can only join one domain. Switches in different domains cannot synchronize VLAN information.
The domain determines the scope of VCMP management devices. All switches added to the domain will be managed by the management device in the domain. There can be only one management device in a domain, but there can be multiple managed devices.
2. Role of VLAN centralized management protocol
(1) Server
As a management role of the VCMP management domain, it is responsible for synchronizing VLAN information to other devices in the same domain through VLAN centralized management protocol messages.
The information about creating and deleting VLANs and modifying VLAN names and descriptions on the server will be propagated throughout the domain.
(2) Client
As a managed role in a VLAN management domain, it belongs to a specific domain and synchronizes VLAN information to the local device based on VLAN centralized management protocol messages sent by the server.
The information about creating or deleting VLANs and modifying VLAN names and descriptions on the client will not be propagated within the domain but will be overwritten by the VLAN information sent by the server.
(3) Transparent
As a transparent transmission role, it is not affected by VLAN management behavior and does not affect other devices in the domain.
Transparent: Directly forward VLAN centralized management protocol packets (only forwarded to Trunk or Hybrid links)
The creation and deletion of VLANs and the modification of VLAN names and descriptions on the Transparent are not affected by the Server and will not be propagated within the domain.
This can meet the needs of some devices that do not want to be managed by VLAN centralized management protocol but need to forward VCMP messages.
(4) Silent
Deployed at the edge of a VLAN management domain, it is not affected by VLAN management behaviors and does not affect other devices in the domain. It can be used to isolate the domain.
After receiving a VLAN centralized management protocol message, Silent directly discards it instead of forwarding it.
The creation and deletion of VLANs and the modification of VLAN names and descriptions on Silent are not affected by the Server and will not be propagated within the domain.
How to use VCMP?
As the scale of enterprise networks continues to expand, the number of switches in the network is increasing, and the VLAN configurations of these switches need to be synchronized to ensure correct data forwarding.
Repeatedly creating and deleting VLANs on these switches is time-consuming and error-prone.
To this end, you can deploy the VLAN centralized management protocol in the enterprise network, determine the VLAN management domain based on the scope to be managed, and then select the aggregation switch or core switch as the VLAN centralized management protocol server.
In this way, you only need to create, delete, or modify the name or description of a VLAN on the aggregation or core switch, and the access switches in the same domain will be modified synchronously, thereby achieving centralized management of VLANs and reducing the workload of configuration and maintenance.
At the same time, if the VLAN management domain does not have an authentication password set when a switch with an empty configuration is inserted, the server will notify it to synchronize the VLAN configuration to achieve plug-and-play.
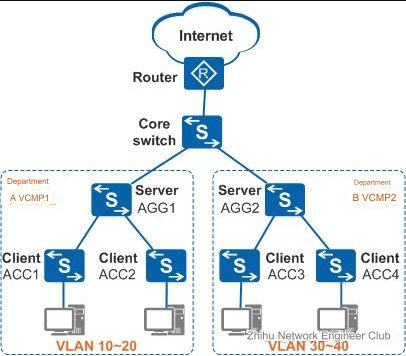
An enterprise has two departments, Department A and Department B, which belong to different Layer 2 networks. Each department is large in scale and requires a lot of VLAN information to be configured and maintained.
To facilitate VLAN configuration and maintenance, VLAN central management protocol can be deployed in Department A and Department B respectively, with management domains VCMP1 and VCMP2. Aggregation switch AGG1 is selected as the server of VCMP1, access switches ACC1 to ACC2 are selected as the clients of VCMP1, aggregation switch AGG2 is selected as the server of VCMP2, and access switches ACC3 to ACC4 are selected as the clients of VCMP2.
In this way, the network administrator only needs to create, delete, or modify the name and description of a VLAN on AGG1 and AGG2 respectively, and ACC1-ACC2 and ACC3-ACC4 will synchronize the VLAN information on AGG1 and AGG2 respectively, thus realizing unified configuration and management of VLANs.
An enterprise has two departments, Department A and Department B, which belong to different Layer 2 networks. Each department is large in scale and requires a lot of VLAN information to be configured and maintained.
To facilitate VLAN configuration and maintenance, the VLAN central management protocol can be deployed in Department A and Department B respectively, with management domains VCMP1 and VCMP2. Aggregation switch AGG1 is selected as the server of VCMP1, access switches ACC1 to ACC2 are selected as the clients of VCMP1, aggregation switch AGG2 is selected as the server of VCMP2, and access switches ACC3 to ACC4 are selected as the clients of VCMP2.
In this way, the network administrator only needs to create, delete, or modify the name and description of a VLAN on AGG1 and AGG2 respectively, and ACC1-ACC2 and ACC3-ACC4 will synchronize the VLAN information on AGG1 and AGG2 respectively, thus realizing unified configuration and management of VLANs.
How to configure VCMP to achieve centralized VLAN management?
1. Network requirements
The branch network of an enterprise is a Layer 2 network. AGG is its aggregation switch, ACC1 to ACC3 are access switches, and ACC1 is used to access external visitors.
As enterprise branches grow in size, network administrators need to configure and maintain a large amount of VLAN information on each switch, which is labor-intensive and error-prone.
Therefore, the administrator hopes to reduce the workload of VLAN configuration and maintenance, but the access rights of external visitors to the branch network need to be restricted. The administrator hopes that the VLAN on ACC1 can be configured and maintained independently.
2. Configuration roadmap
VLAN central management protocol can be deployed in this enterprise branch network. Set the aggregation switch AGG as the server and the access switches ACC2 to ACC3 as the clients. To prevent ACC1 from being managed by VLAN central management protocol, set it to Silent.
In this way, you only need to modify the VLAN information on the AGG, and the information will be automatically sent to ACC1~ACC3 in the enterprise branch network.
ACC2~ACC3 will automatically synchronize the VLAN information on AGG, while ACC1 is not affected by VLAN central management protocol, which not only reduces the workload of modifying the same VLAN information on multiple switches but also ensures the VLAN independence of ACC1.
At the same time, to avoid the trouble of manually setting the link type, configure automatic negotiation of the link type through LNP.

The configuration roadmap is as follows:
(1) Configure LNP to implement automatic link type negotiation and simplify user configuration.
(2) Specify the role of each device to determine the VCMP management scope and management and managed objects.
(3) Configure VCMP-related parameters on the devices that play the server and client roles, including authentication passwords and device IDs, to ensure secure communication and identity recognition between the server and client.
(4) Enable VLAN central management protocol to make the function take effect.
3. Operation steps
(1) Configuring automatic negotiation of link type through LNP
By default, LNP is enabled globally and on interfaces. All interfaces use LNP to automatically negotiate link types.
You can run the display lnp summary command to check whether the link type auto-negotiation function is enabled globally and on interfaces of the switch (pay attention to the Global LNP and link-type(C) fields in the displayed information respectively), and check the link type of the interface (pay attention to the link-type(N) field in the displayed information):
If the link type auto-negotiation function is not enabled globally or on an interface, perform the following steps to configure it:
# Enable the link type auto-negotiation function globally. The configurations of ACC1, ACC2, and ACC3 are similar to that of AGG and are not mentioned here.
<HUAWEI> system-view
[HUAWEI] sysname AGG
[AGG] undo lnp disable
# Enable the link type auto-negotiation function on the interface. The configurations of ACC1, ACC2, and ACC3 are similar to that of AGG and are not mentioned here.
[AGG] interface GigabitEthernet 0/0/1
[AGG-GigabitEthernet0/0/1] undo port negotiation disable
[AGG-GigabitEthernet0/0/1] port link-type negotiation-desirable
[AGG-GigabitEthernet0/0/1] quit
[AGG] interface GigabitEthernet 0/0/2
[AGG-GigabitEthernet0/0/2] undo port negotiation disable
[AGG-GigabitEthernet0/0/2] port link-type negotiation-desirable
[AGG-GigabitEthernet0/0/2] quit
[AGG] interface GigabitEthernet 0/0/3
[AGG-GigabitEthernet0/0/3] undo port negotiation disable
[AGG-GigabitEthernet0/0/3] port link-type negotiation-desirable
[AGG-GigabitEthernet0/0/3] quit
If the link type auto-negotiation function is enabled globally and on interfaces, but the link type of the interface connecting switches is access, to ensure the normal operation of VLAN central management protocol, you can run the port link-type { trunk | hybrid } command to manually specify the link type of the interface.
(2) Specify the role of each device
# Configure the AGG role as Server.
[AGG] vcmp role server
# Configure the role of ACC1 as silent.
[ACC1] vcmp role silent
# Configure the role of ACC2 as Client.
[ACC2] vcmp role client
# Configure the role of ACC3 as Client.
[ACC3] vcmp role client
(3) Configuring VLAN central management protocol parameters on the server and client
# Configure its management domain, device ID, and authentication password on the AGG.
[AGG] vcmp domain vd1
[AGG] vcmp device-id server
[AGG] vcmp authentication sha2-256 password Hello
# Configure its management domain and authentication password on ACC2.
[ACC2] vcmp domain vd1
[ACC2] vcmp authentication sha2-256 password Hello
# Configure its management domain and authentication password on ACC3.
[ACC3] vcmp domain vd1
[ACC3] vcmp authentication sha2-256 password Hello
(4) Enabling VCMP
By default, the VLAN centralized management protocol is enabled on the interface and does not need to be enabled again. However, to prevent VCMP packets from affecting PC terminals, you can disable VCMP on the interface that connects the client to the PC terminal.
[ACC2] interface GigabitEthernet 0/0/2
[ACC2-GigabitEthernet0/0/2] vcmp disable
[ACC2-GigabitEthernet0/0/2] quit [ACC3] interface GigabitEthernet 0/0/2
[ACC3-GigabitEthernet0/0/2] vcmp disable
[ACC3-GigabitEthernet0/0/2] quit
(5) Verifying the configuration
After the above configuration is complete, run the display VLAN central management protocol status command to view its configuration information, including the VLAN management domain name, device role, device ID, configuration serial number, and domain password.



