OSPF packet analysis provides a clear view of the protocol’s interaction mechanisms by examining the structure of messages, helping to fully grasp the communication process.
Verifying theoretical knowledge through OSPF packet analysis deepens understanding and fosters the ability to independently examine networking data, enhancing self-learning skills.
This article focuses on OSPF packet analysis. Those unfamiliar with the theoretical background are encouraged to review the basics before diving into packet-level details.
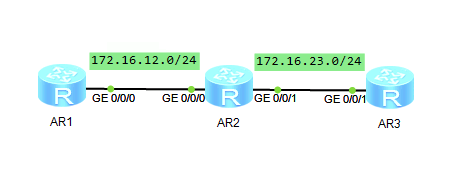
Experimental Topology for OSPF Packet Analysis
1. Five types of packages
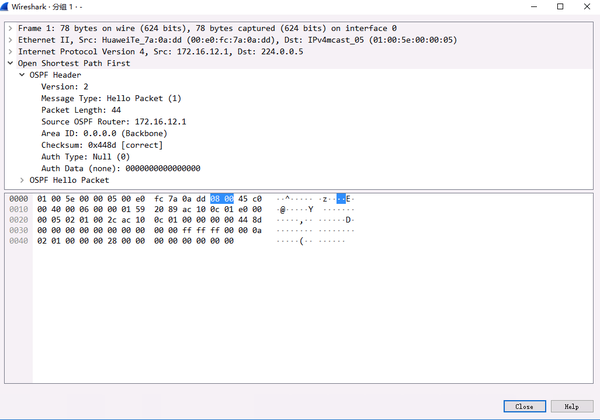
1.1. HELLO Message in OSPF Packet Analysis
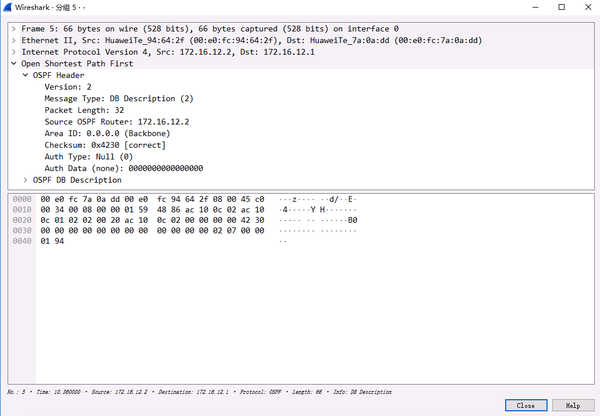
1.2.DBD message
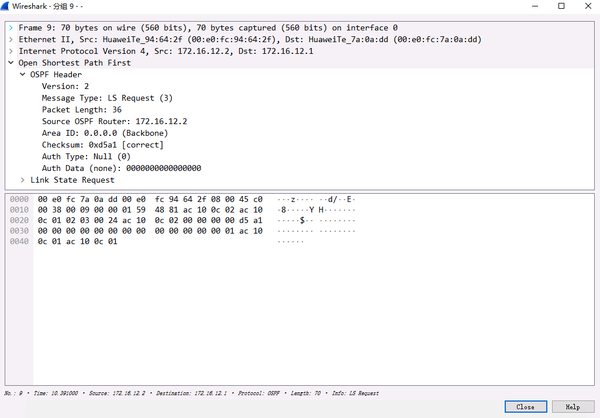
1.3.LSR Message
1.4.LSU message
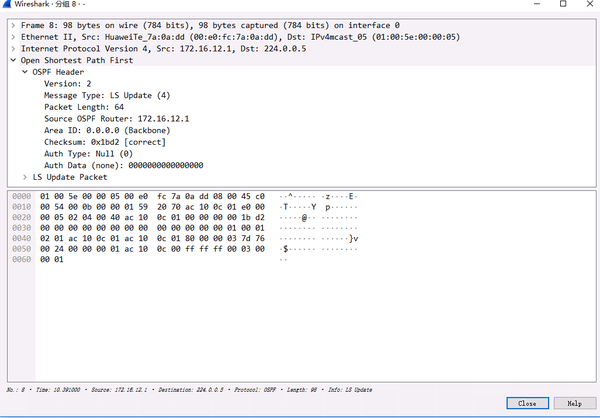
1.5.LSACK message
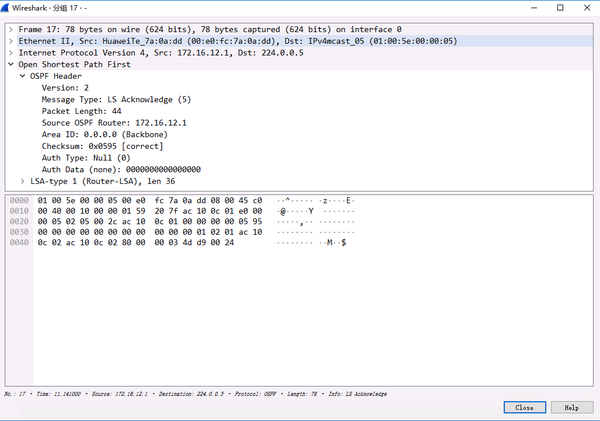
2. Seven states
2.1.DOWN
No OSPF-related messages are exchanged, and the neighbor status is empty.
2.2. INIT State and Router-ID Verification in OSPF Packet Analysis
2.2.1. Check router-id
1) Capture the packet and check the ROUTER-ID in the message
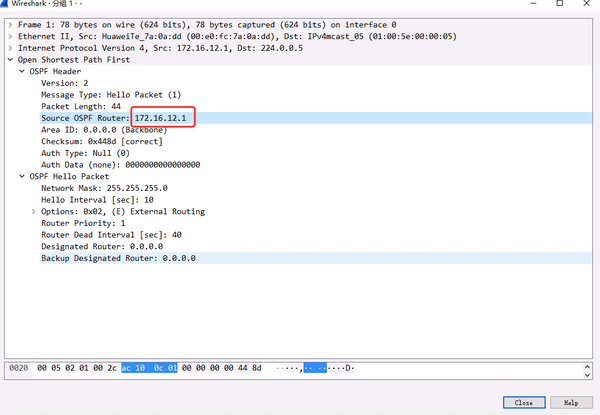
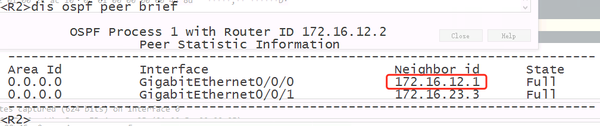
2) Check the router-id of the neighbor relationship on the device
2.2.2. Manually modify router-id
1) Configuration Commands
ospf 1 router-id 1.1.1.1
reset ospf process
2) Capture the packet and check the ROUTER-ID in the message
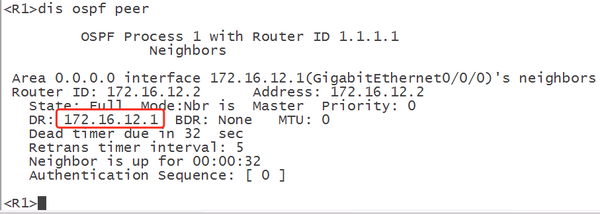
3) Check the router-id that takes effect after the neighbor modification on the device
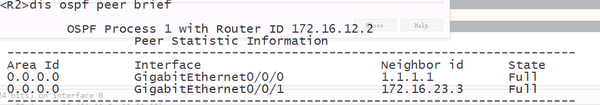
2.2.3. INIT → two way conditions
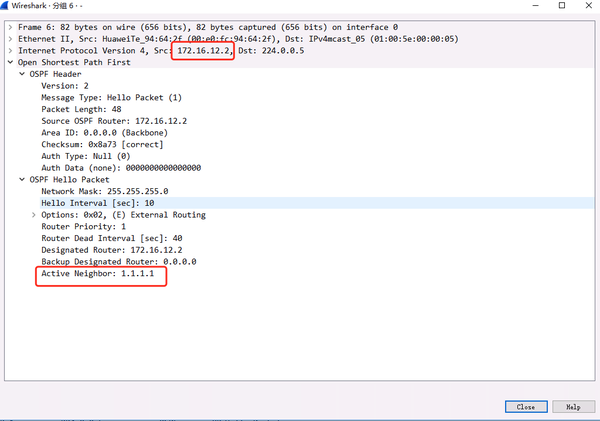
The hello message received from the neighboring device contains its own router-id (Active Neighbor in the message)
The router-id of 1.1.1.1 in the HELLO packet sent by R2
2.3. TWO-WAY State: DR and BDR Roles in OSPF Packet Analysis
DR and BDR in HELLO message
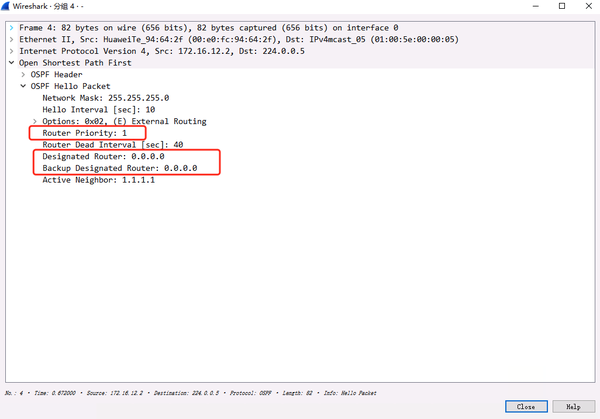
2.3.1. DR and BDR have not been elected yet, HELLO message capture
Priority is not adjusted, default is 1
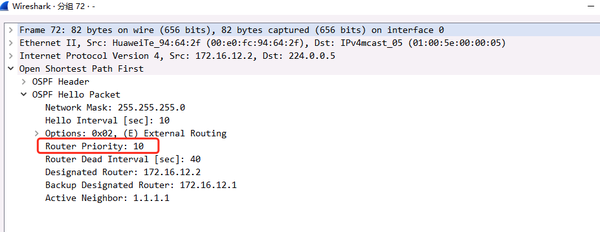
2.3.2. Adjust the interface priority to 10
Adjusting the OSPF DR Priority
1) Configuration Commands
int g0/0/0
ospf dr-priority 10
2) The priority of packet capture is 10
2.3.3. Effects of Setting DR Priority to Zero in OSPF Packet Analysis
1) Configuration Commands
Adjust R2’s DR priority to 0
int g0/0/0
ospf dr-priority 0
2) Capture the packet and view it
R2 was originally the DR, but now it does not participate in the DR election. R1 becomes the DR, and there is no BDR.

2.4. EXSTART State: DBD Message Negotiation in OSPF Packet Analysis
2.4.1.MS bit in DBD message
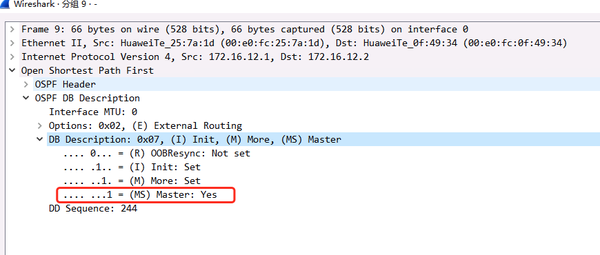
1) The master-slave DBD has not yet been negotiated
The first DBD message MS is always 1
The first DBD message on R1
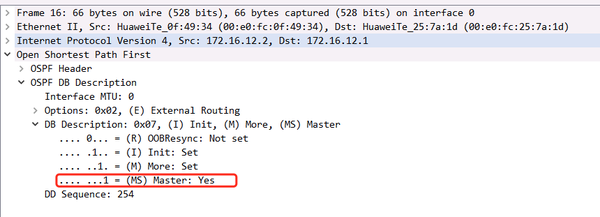
The first DBD message on R2
2) Negotiated DBD
After the negotiation is completed, there must be a device that sends MS=0;
R1 MS is 0, then R1 is a slave device
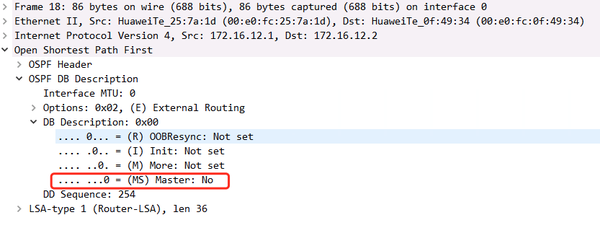
R2 MS is 1, this is when R2 is the primary device
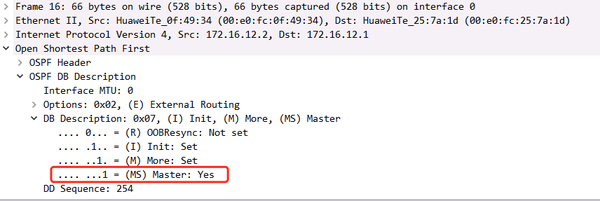
2.4.2. Sequence Number in DBD Message
R2 sends seq 281
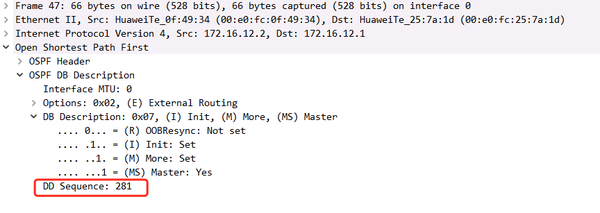
R1 confirmed seq 281
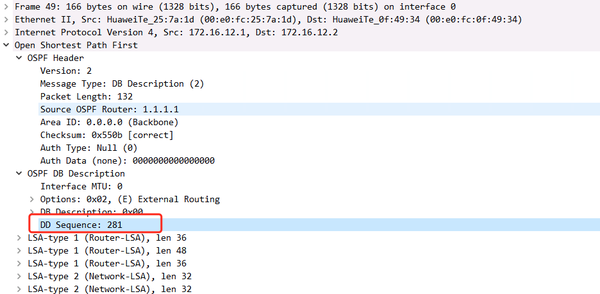
2.5. EXCHANGE State: OSPF Packet Analysis of M Bit in DBD Messages
The M bit in the DBD message
M=1, indicating that the DBD message has not been sent yet
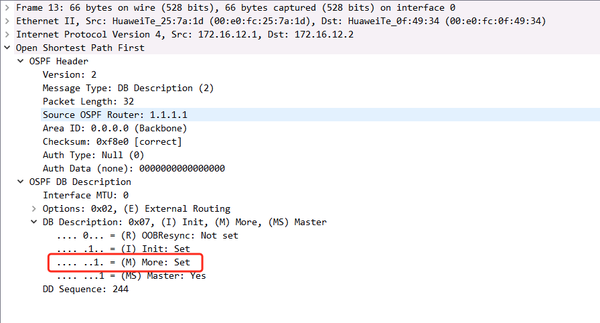
M=0, indicating that the DBD message has been sent.
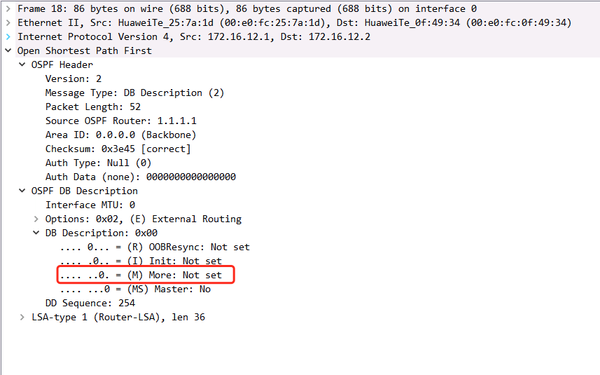
2.6.LOADING
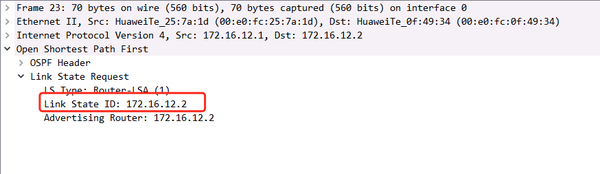
R1 sends LSR to request link information of 172.16.12.2
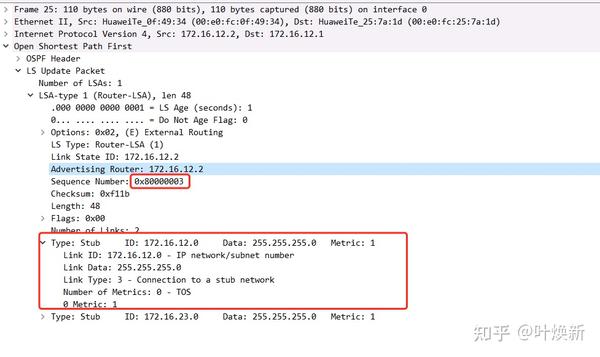
R2 responds to the request
The LSA in the LSU responds to the peer’s request. The LSA sequence number is 0x80000003.
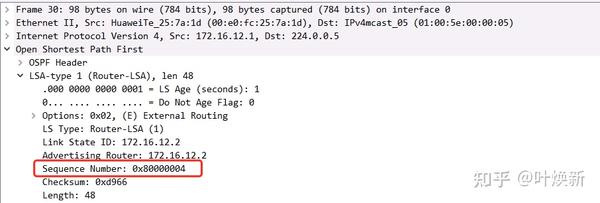
LSACK, confirming that the LSA sequence number is 0x80000004 (+1)
2.7.FULL
Messages in a stable state
10S HELLO stable state
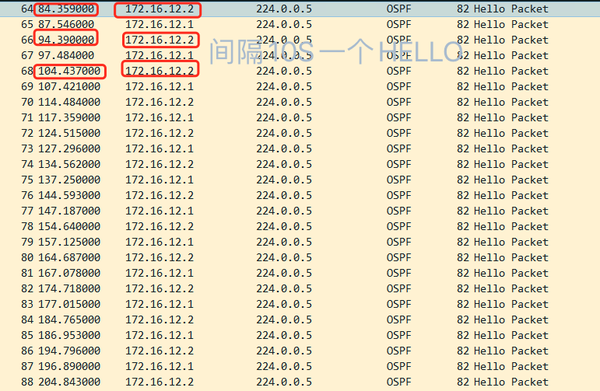
After about 1800 seconds, LSU LSACK is flooded again.
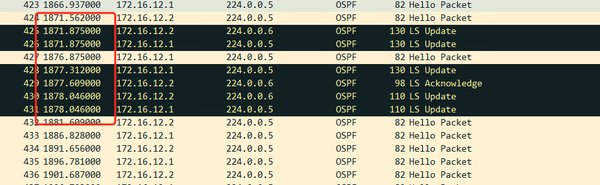
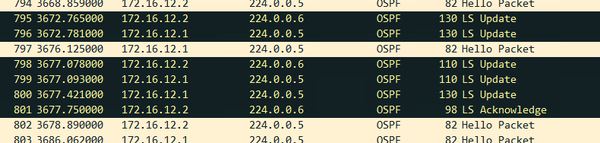
After another 1800 seconds, LSU LSACK is flooded again
Learning may seem dull at first, but OSPF packet analysis adds a practical dimension that makes it intriguing. By combining theoretical knowledge with packet-level investigation, you can uncover the inner workings of networking protocols, turning learning into a more engaging and insightful experience.



