To fully understand packet analysis, it is essential to grasp how computers communicate with each other. This section explores the fundamentals of network protocols, the Open Systems Interconnection (OSI) model, data encapsulation within network data frames, and the hardware that supports these processes.
Modern networks are made up of a variety of systems running on many different platforms. To aid this communication, we use a set of common languages called protocols. Common protocols include Transmission Control Protocol (TCP), Internet Protocol (IP), Address Resolution Protocol (ARP), and Dynamic Host Configuration Protocol (DHCP). A protocol stack is a logical grouping of protocols that work together. One of the best ways to understand protocols is to think of them as similar to the rules that govern spoken or written human languages. Every language has rules, such as how verbs should be conjugated, how people should be greeted, and even how to properly thank someone. Protocols work in much the same fashion, allowing us to define how packets should be routed, how to initiate a connection, and how to acknowledge the receipt of data.
A protocol can be extremely simple or highly complex, depending on its function. Although the various protocols are often drastically different, many protocols commonly address the following issues:
Connection initiation Is it the client or server initiating the connection?
What information must be exchanged prior to communication?
Negotiation of connection characteristics Is the communication of the
protocol encrypted? How are encryption keys transmitted between communicating
hosts?
Data formatting How is the data contained in the packet ordered? In
what order is the data processed by the devices receiving it?
Error detection and correction What happens in the event that a packet
takes too long to reach its destination? How does a client recover if it cannot
establish communication with a server for a short duration?
Connection termination How does one host signify to the other that
communication has ended? What final information must be transmitted
in order to gracefully terminate communication?
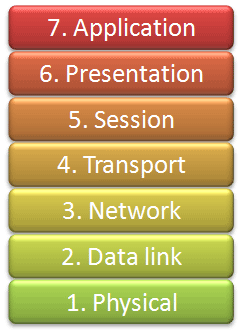
Each OSI model layer has a specific function, as follows: Application layer (layer 7) The topmost layer of the OSI model provides a means for users to actually access network resources. This is the only layer typically seen by end users, as it provides the interface that is the base for all of their network activities. Presentation layer (layer 6) This layer transforms the data it receives into a format that can be read by the application layer. The data encoding and decoding done here depends on the application layer protocol that is sending or receiving the data. The presentation layer also handles several forms of encryption and decryption used for securing data. Session layer (layer 5) This layer manages the dialogue, or session between two computers. It establishes, manages, and terminates this connection among all communicating devices. The session layer is also responsible for establishing whether a connection is duplex or half-duplex, and for gracefully closing a connection between hosts, rather than dropping it abruptly. Protocols are separated according to their functions based on the industry-standard OSI reference model. The OSI model divides the network communications process into seven distinct layers, as shown in Figure 1-1. This hierarchical model makes it much easier to understand network communication. The application layer at the top represents the actual programs used to access network resources. The bottom layer is the physical layer, through which the actual network data travels. The protocols at each layer work together to ensure data is properly handled by the protocols at layers above and below it.
Node: The OSI model was originally published in 1983by the International Organization for Standardization(ISO) as a document called ISO 7498.The OSI model is no more than an industryrecommendedstandard. Protocol developers arenot required to follow it exactly. And the OSImodel is not the only networking model thatexists; for example, some people prefer the Departmentof Defense (DoD) model, also known as theTCP/IP model.
Each OSI model layer has a specific function, as follows:
Application layer (layer 7) The topmost layer of the OSI model providesa means for users to actually access network resources. This is the onlylayer typically seen by end users, as it provides the interface that is thebase for all of their network activities.
Presentation layer (layer 6) This layer transforms the data it receivesinto a format that can be read by the application layer. The data encodingand decoding done here depends on the application layer protocolthat is sending or receiving the data. The presentation layer also handlesseveral forms of encryption and decryption used for securing data.
Session layer (layer 5) This layer manages the dialogue, or session betweentwo computers. It establishes, manages, and terminates this connectionamong all communicating devices. The session layer is also responsiblefor establishing whether a connection is duplex or half-duplex, and forgracefully closing a connection between hosts, rather than dropping itabruptly.
Transport layer (layer 4) The primary purpose of the transport layer isto provide reliable data transport services to lower layers. Through flowcontrol, segmentation/desegmentation, and error control, the transportlayer makes sure data gets from point to point error-free. Because ensuringreliable data transportation can be extremely cumbersome, the OSImodel devotes an entire layer to it. The transport layer utilizes bothconnection-oriented and connectionless protocols. Certain firewalls andproxy servers operate at this layer.
Network layer (layer 3) This layer is responsible for routing data betweenphysical networks, and it is one of the most complex of the OSI layers. Itis responsible for the logical addressing of network hosts (for example,through an IP address). It also handles packet fragmentation, and in somecases, error detection. Routers operate at this layer.
Data link layer (layer 2) This layer provides a means of transportingdata across a physical network. Its primary purpose is to provide anaddressing scheme that can be used to identify physical devices (forexample, MAC addresses). Bridges and switches are physical devices thatoperate at the data link layer.
Physical layer (layer 1) The layer at the bottom of the OSI model is thephysical medium through which network data is transferred. This layerdefines the physical and electrical nature of all hardware used, includingvoltages, hubs, network adapters, repeaters, and cabling specifications.The physical layer establishes and terminates connections, provides ameans of sharing communication resources, and converts signals fromdigital to analog and vice versa.
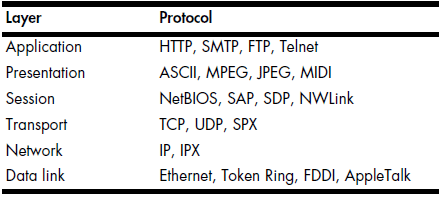
Table 1-1 lists some of the more common protocols used at each individuallayer of the OSI model.
Table 1-1: Typical Protocols Used in Each Layer of the OSI Model

Although the OSI model is no more than a recommended standard, youshould know it by heart. As we progress through this book, you will find thatthe interaction of protocols on different layers will shape your approach tonetwork problems. Router issues will soon become “layer 3 problems” andsoftware issues will be recognized as “layer 7 problems.”
NOTE In discussing our work, a colleague told me about a user complaining that he could notaccess a network resource. The issue was the result of the user entering an incorrectpassword. My colleague referred to this as a “layer 8 issue.” Layer 8 is the unofficialuser layer. This term is commonly used
among those who live at the packet level.How does data flow through the OSI model? The initial data transfer ona network begins at the application layer of the transmitting system. Dataworks its way down the seven layers of the OSI model until it reaches thephysical layer, at which point the physical layer of the transmitting systemsends the data to the receiving system. The receiving system picks up the dataat its physical layer, and the data proceeds up the remaining layers of thereceiving system to the application layer at the top.
Services provided by various protocols at any given level of the OSI modelare not redundant. For example, if a protocol at one layer provides a particularservice, then no other protocol at any other layer will provide this sameservice. Protocols at different levels may have features with similar goals, butthey will function a bit differently.
Protocols at corresponding layers on the sending and receiving computersare complementary. For example, if a protocol on layer 7 of the sendingcomputer is responsible for encrypting the data being transmitted, the correspondingprotocol on layer 7 of the receiving machine is expected to beresponsible for decrypting that data.
Figure 1-2 shows a graphical representation of the OSI model as it relatesto two communicating clients. You can see communication going from top tobottom on one client, and then reversing when it reaches the second client.
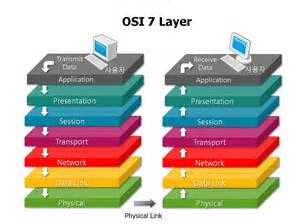
Figure 1-2: Protocols working at the same layer on both the sending and receiving systems
Each layer in the OSI model is capable of communicating with only thelayers directly above and below it. For example, layer 2 can send and receivedata only from layers 1 and 3.
The protocols on different layers of the OSI model communicate with theaid of data encapsulation. Each layer in the stack is responsible for adding aheader or footer—extra bits of information that allow the layers to communicate—to the data being communicated. For example, when the transportlayer receives data from the session layer, it adds its own header informationto that data before passing it to the next layer.
The encapsulation process creates a protocol data unit (PDU), which includesthe data being sent and all header or footer information added to it. As datamoves down the OSI model, the PDU changes and grows as header andfooter information from various protocols is added to it. The PDU is in itsfinal form once it reaches the physical layer, at which point it is sent to thedestination computer. The receiving computer strips the protocol headersand footers from the PDU as the data climbs up the OSI layers. Once thePDU reaches the top layer of the OSI model, only the original data remains.
NOTE The term packet refers to a complete PDU that includes header and footer informationfrom all layers of the OSI model.
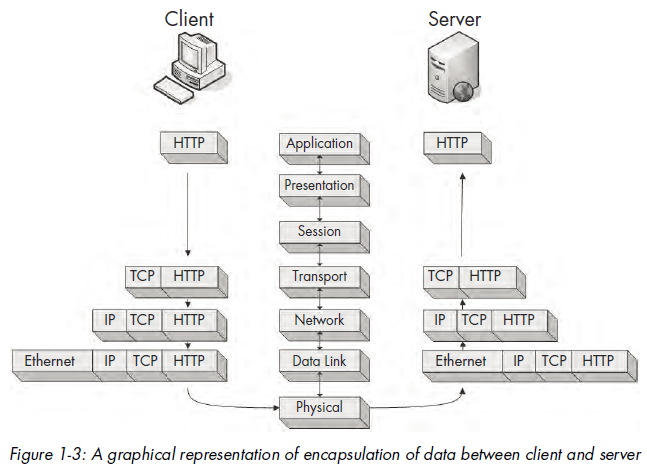
Understanding how encapsulation of data works can be a bit confusing,so we’ll look at a practical example of a packet being built, transmitted, andreceived in relation to the OSI model. Keep in mind that as analysts, we don’toften talk about the session or presentation layers, so those will be absent inthis example (and the rest of this book).
In this scenario, we are on a computer that is attempting to browse tohttp://www.google.com/. For this process to take place, we must generate arequest packet that is transmitted from our source client computer to thedestination server computer. This scenario assumes that a TCP/IP communicationsession has already been initiated. Figure 1-3 illustrates the dataencapsulationprocess in this example.
We begin on our client computer at the application layer. We are browsingto a website, so the application layer protocol being used is HTTP, whichwill issue a command to download the file index.html from google.com.
Once our application layer protocol has dictated what we want to accomplish,our concern is with getting the packet to its destination. The data inour packet is passed down the stack to the transport layer. HTTP is an applicationlayer protocol that utilizes, or sits on, TCP. Therefore, TCP serves asthe transport layer protocol used to ensure reliable delivery of the packet.As a result, a TCP header is generated. This TCP header includes sequencenumbers and other data that is appended to the packet, and ensures that thepacket is properly delivered.
NOTE We often say that one protocol “sits on” another protocol because of the top-down designof the OSI model. An application protocol such as HTTP provides a particular serviceand relies on TCP to ensure delivery of its service. As you will learn, DNS sits on UDP,and TCP sits on IP.
Having done its job, TCP hands the packet off to IP, which is the layer 3protocol responsible for the logical addressing of the packet. IP creates aheader containing logical addressing information and passes the packet alongto Ethernet on the data link layer. Physical Ethernet addresses are stored inthe Ethernet header. The packet is now fully assembled and passed to thephysical layer, where it is transmitted as zeros and ones across the network.
The completed packet traverses the network cabling system, eventuallyreaching the Google web server. The web server begins by reading the packetfrom the bottom up, meaning that it first reads the data link layer, whichcontains the physical Ethernet addressing information that the network carduses to determine that the packet is intended for a particular server. Oncethis information is processed, the layer 2 information is stripped away, andthe layer 3 information is processed.
The IP addressing information is read in the same manner as the layer 2information to ensure proper addressing and that the packet is not fragmented.This data is also stripped away so that the next layer can be processed.
Layer 4 TCP information is now read to ensure that the packet has arrivedin sequence. Then the layer 4 header information is stripped away, leavingonly the application layer data, which can be passed to the web server applicationhosting the website. In response to this packet from the client, theserver should transmit a TCP acknowledgment packet so the client knowsits request was received followed by the index.html file.
All packets are built and processed as described in this example, regardlessof which protocols are used. But at the same time, keep in mind that notevery packet on a network is generated from an application layer protocol, soyou will see packets that contain only information from layer 2, 3, or 4 protocols.
Now it’s time to look at network hardware, where the dirty work is done.We’ll focus on just a few of the more common pieces of network hardware:hubs, switches, and routers.
Hubs A hub is generally a box with multiple RJ-45 ports, like the NETGEAR hubshown in Figure 1-4. Hubs range from very small 4-port devices to larger 48-portones designed for rack mounting in a corporate environment.

Figure 1-4: A typical 4-port Ethernet hub
Because hubs can generate a lot of unnecessary network traffic and arecapable of operating only in half-duplex mode (they cannot send and receivedata at the same time), you won’t typically see them used in most modern orhigh-density networks (switches are used instead). However, you should knowhow hubs work, since they will be very important to packet analysis when usingthe “hubbing out” technique discussed in Chapter 2.
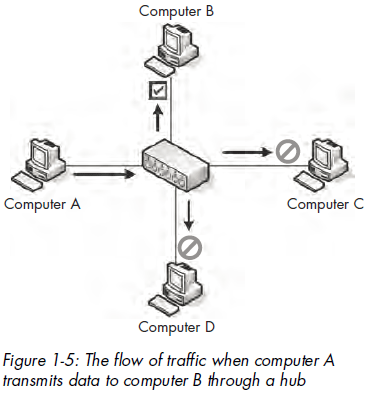
A hub is no more than a repeating device that operates on the physicallayer of the OSI model. It takes packets sent from one port and transmits(repeats) them to every other port on the device. For example, if a computeron port 1 of a 4-port hub needs to send data to a computer on port 2, thehub sends those packets to ports 1, 2, 3, and 4. The clients connected toports 3 and 4 examine the destination Media Access Control (MAC) addressfield in the Ethernet header of the packet, and they see that the packet is notfor them, so they drop (discard) the packet. Figure 1-5 illustrates an examplein which computer A is transmitting data to computer B. When computer Asends this data, all computers connected to the hub receive it. Only computer Bactually accepts the data; the other computers discard it.
As an analogy, suppose that you sent an email with the subject line “Attentionall marketing staff ” to every employee in your company, rather than toonly those people who work in the marketing department. The marketingdepartment employees will know it is for them, and they will probably open
it. The other employees will see that it is not for them, and they will probablydiscard it. You can see how this would result in a lot of unnecessary communicationand wasted time, yet this is exactly how a hub functions.
The best alternatives to hubs in production and high-density networksare switches, which are full-duplex devices that can send and receive datasynchronously.
Switches
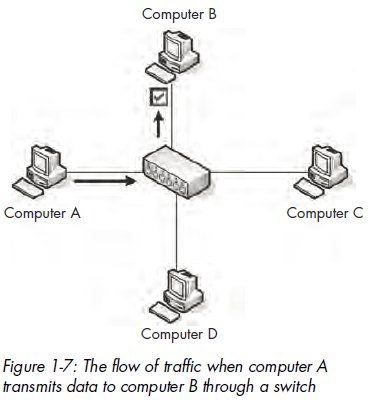
Like a hub, a switch is designed to repeat packets. However, unlike a hub,rather than broadcasting data to every port, a switch sends data to only thecomputer for which the data is intended. Switches look just like hubs, asshown in Figure 1-6.

Figure 1-6: A rack-mountable 24-port Ethernet switch
Several larger switches on the market, such as Cisco-branded ones, aremanaged via specialized, vendor-specific software or web interfaces. Theseswitches are commonly referred to as managed switches. Managed switchesprovide several features that can be useful in network management, includingthe ability to enable or disable specific ports, view port specifics, make configurationchanges, and remotely reboot.
Switches also offer advanced functionality when it comes to handlingtransmitted packets. In order to be able to communicate directly with specificdevices, switches must be able to uniquely identify devices based on their MACaddresses, which means that they must operate on the data link layer of theOSI model.
Switches store the layer 2 address of every connected device in a CAMtable, which acts as a kind of traffic cop. When a packet is transmitted, theswitch reads the layer 2 header information in the packet and, using the CAMtable as reference, determines to which port(s) to send the packet. Switchessend packets only to specific ports, thus greatly reducing network traffic.
Figure 1-7 illustrates traffic flow through a switch. In this figure, computerA is sending data to only the intended recipient: computer B. Multipleconversations can happen on the network at the same time, but informationis communicated directly between the switch and intended recipient, notbetween the switch and all connected computers.
Routers
A router is an advanced network device with a much higher level of functionalitythan a switch or a hub. A router can take many shapes and forms, butmost have several LED indicator lights on the front and a few network portson the back, depending on the size of the network. Figure 1-8 shows anexample of a router.
Routers operate at layer 3 of the OSI model, where they are responsiblefor forwarding packets between two or more networks. The process routersuse to direct the flow of traffic among networks is called routing. Several typesof routing protocols dictate how different types of packets are routed to othernetworks. Routers commonly use layer 3 addresses (such as IP addresses) touniquely identify devices on a network.

Figure 1-8: A low-level Cisco router suitable for use in a small to mid-sized network
One way to illustrate the concept of routing is by using the analogy of aneighborhood with several streets. Think of the houses, with their addresses,as computers, and each street as a network segment, as shown in Figure 1-9.From your house on your street, you can easily communicate with yourneighbors in the other houses on the street. This is similar to the operationof a switch that allows communication among all computers on a networksegment. However, communicating with a neighbor on another street is likecommunicating with a computer that is not on the same segment.
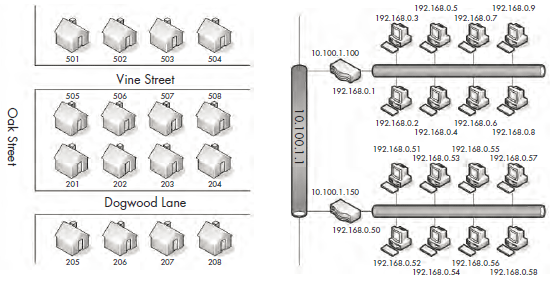
Figure 1-9: Comparison of a routed network to neighborhood streets
Referring to Figure 1-9, let’s say that you’re sitting at 503 Vine Street andneed to get to 202 Dogwood Lane. In order to do this, you must cross ontoOak Street, and then onto Dogwood Lane. Think of this as crossing networksegments. If the device at 192.168.0.3 needs to communicate with the deviceat 192.168.0.54, it must cross a router to get to the 10.100.1.1 network, andthen cross the destination network segment’s router before it can get to thedestination network segment.
The size and number of routers on a network will typically depend onthe network’s size and function. Personal and home-office networks may haveonly a small router located at the center of the network. A large corporatenetwork might have several routers spread throughout various departments,all connecting to one large central router or layer 3 switch (an advanced typeof switch that also has built-in functionality to act as a router).
As you begin looking at more and more network diagrams, you will cometo understand how data flows through these various points. Figure 1-10 showsthe layout of a very common form of routed network. In this example, twoseparate networks are connected via a single router. If a computer on networkA wishes to communicate with a computer on network B, the transmitteddata must go through the router.
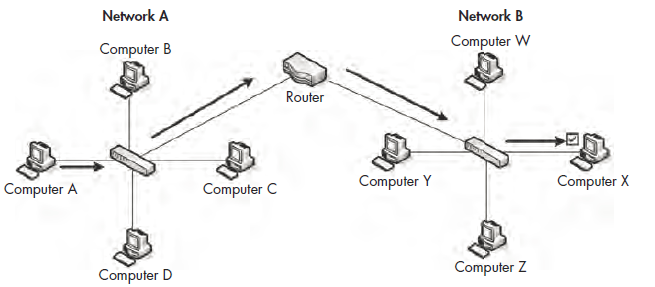
Figure 1-10: The flow of traffic when computer A transmits data to computer X through a router



