We have looked at four different ways to capture network traffic in a switched environment. We can add one more if we consider simply installing a packet sniffing application on a single device from which we want to capture traffic (the direct install method). Given these five methods, it can be a bit confusing to determine which one is the most appropriate. Table 2-2 provides some general guidelines for each method.
Table 2-2: Guidelines for Packet Sniffing in a Switched Environment
| Port mirroring | • Usually preferred because it leaves no network footprint and no additional packets are generated as a result of it. • Can be configured without taking the client offline, which is convenient when mirroring router or server ports. |
| Hubbing out | • Ideal when you are not concerned about taking the host temporarily offline. • Ineffective when you must capture traffic from multiple hosts, as collisions and dropped packets will be imminent. • Can result in lost packets on modern 100/1000Mbps hosts because most true hubs are only 10Mbps. |
| Using a tap | • Ideal when you are not concerned about taking the host temporarily offline. • The only option when you need to sniff traffic from a fiber-optic connection. • Since taps are made for the task at hand and are up to par with modern network speeds, this method is superior to hubbing out. • May be cost prohibitive when budgets are tight. |
| ARP cache poisoning | • Considered very sloppy, as it involves injecting packets onto the network in order to reroute traffic through your sniffer. • Can be effective when you need to grab a quick capture of traffic from a device without taking it offline and where port mirroring is not an option. |
| Direct install | • Usually not recommended because if there is an issue with a host, that issue could cause packets to be dropped or manipulated in such a way that they are not represented accurately. • The NIC of the host does not need to be in promiscuous mode. • Best for test environments, examining/baselining performance, and examining capture files created elsewhere. |
As analysts, we need to be as stealthy as possible. In a perfect world, we collect the data we need without leaving a footprint. Just as forensic investigators don’t want to contaminate a crime scene, we don’t want to contaminate our captured network traffic.
As we step through practical scenarios in later chapters, we’ll discuss the best ways to capture the data we require on a case-by-case basis. For the time being, the flowchart in Figure 2-15 should help you to decide on the bestmethod to use for capturing traffic. Remember that this flowchart is simply ageneral reference, and it does not cover every possible iteration of tapping into the wire.
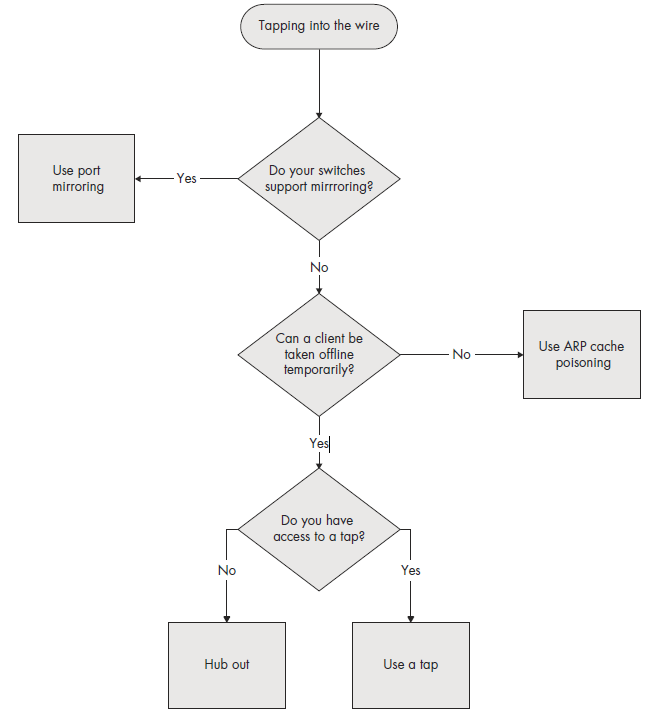
Figure 2-15: A diagram to help determine which method is best for tapping into the wire



